Stay on top of CVEs with instantaneous cybersecurity alerts

CVE (Common Vulnerabilities and Exposures) reports serve as the backbone of cybersecurity, offering a standardized methodology for identifying and managing vulnerabilities in computer systems and software. These reports are a linchpin for organizations and security professionals, enabling swift detection and remediation of security flaws.
The repository for these invaluable reports is the centralized CVE database, diligently maintained and published by the MITRE Corporation. This blog discusses how to keep track of any new updates to the CVE list. Timely CVE alerts are key in helping organizations and security professionals stay informed about security threats and vulnerabilities and take appropriate actions to mitigate them.
Where are CVE reports available and how do CVE alerts help?
The primary source for tracking CVE reports is the official CVE database, which the MITRE Corporation maintains. You can visit the CVE website (https://cve.mitre.org/), search for specific CVE entries, or browse the database to find vulnerabilities relevant to your systems or software. Additionally, third-party vulnerability databases and scanning tools track and report on CVEs.
Threat intelligence platforms collect and analyze data from various sources, including CVE reports, to provide insights into emerging threats. Some tools and services aggregate CVE feeds from various sources and provide a consolidated view of CVE information. These just elaborate that effective CVE tracking is critical to a proactive cybersecurity strategy.
Some other reliable sources of CVE reports include:
- The National Vulnerability Database (NVD) is maintained by the National Institute of Standards and Technology (NIST) is one of the most comprehensive sources for CVE reports. It provides detailed information about vulnerabilities, including severity scores and mitigations.
- CVE Details offers a user-friendly interface to access CVE information, including statistics, trends, and detailed vulnerability information
- Cybersecurity and Infrastructure Security Agency (CISA), is a U.S. government agency responsible for safeguarding against cyber threats. CISA provides cybersecurity guidance, coordinates responses to cyber incidents, and offers various resources, including CVE reports.
What’s inside a CVE report?
CVE reports follow a specific standard format that includes the following information:
- A unique CVE identifier (e.g., CVE-2023-12345).
- A brief description of the vulnerability.
- Information about the affected software or hardware.
- The severity of the vulnerability.
- References to additional resources or advisories related to the vulnerability.
- Any available solutions or patches to mitigate the vulnerability.
- The date when the CVE report was published.
CVE identifiers to communicate about vulnerabilities, track their status, and coordinate efforts to address them. CVE reports may be updated to reflect new information about vulnerabilities, such as additional attack vectors or mitigations.
How to get real-time alerts when the CVE list is updated?
You can use website change monitoring tools to automatically track updates to the CVE list to ensure timely awareness of newly published vulnerabilities. With tools like Distill, you can configure custom conditions to track vulnerability and threat updates. This allows you to reduce the noise of getting false alerts. With APIs, you can even configure workflows to map these CVE alerts to your in-house security systems. This will allow your cybersecurity teams to respond to new threats.
How do website monitoring tools track CVE updates in real-time?
A monitor can be set up to track a specific CVE list web page or even parts of the page. Users set parameters like keywords and monitoring frequency. Whenever a change is detected on the webpage, the tool will send an alert. The changes you can track can include:
- Tracking updates to the CVE list
- Announcement of a new threat or vulnerability
- Alerts on solutions or patches to mitigate the vulnerability
- The list of software, hardware, or systems that are vulnerable to the CVE
- Details about the vulnerability
Set up Distill for Vulnerability alerts
As a part of active efforts to find vulnerabilities, improve threat intelligence, and ensure compliance with security standards, organizations track CVE reports and Known Exploited Vulnerabilities Catalogs.
You can use Distill to track any updates to the list of security vulnerabilities. First, you’ll have to download the Distill extension for your web browser. It is available on Chrome, Firefox, Opera, and Microsoft Edge
Four simple Steps to track CVE reports with Distill
Step 1: Navigate to the vulnerabilities catalog page. In our case, let’s track CISA’s page, it lists the latest 10 entries of the CVE report. Click on the Distill extension from your browser, and click “Monitor parts of page.”
Note: You can even use the drop-down to monitor full page if that’s your requirement.
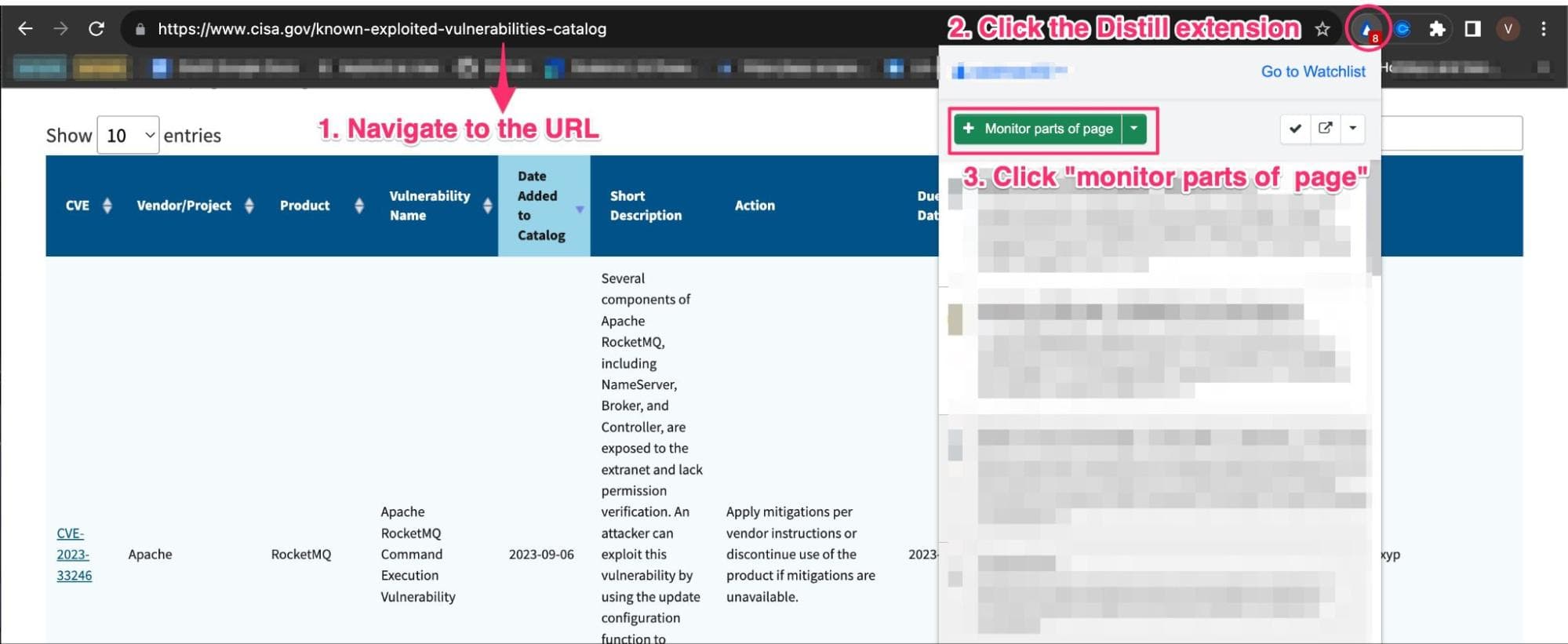
Step 2: Distill’s visual selector opens up, allowing you to select the parts of the page you want to track. Here, you’d want to start by clicking on an element in the table and then expanding your selection, as shown in the image below.
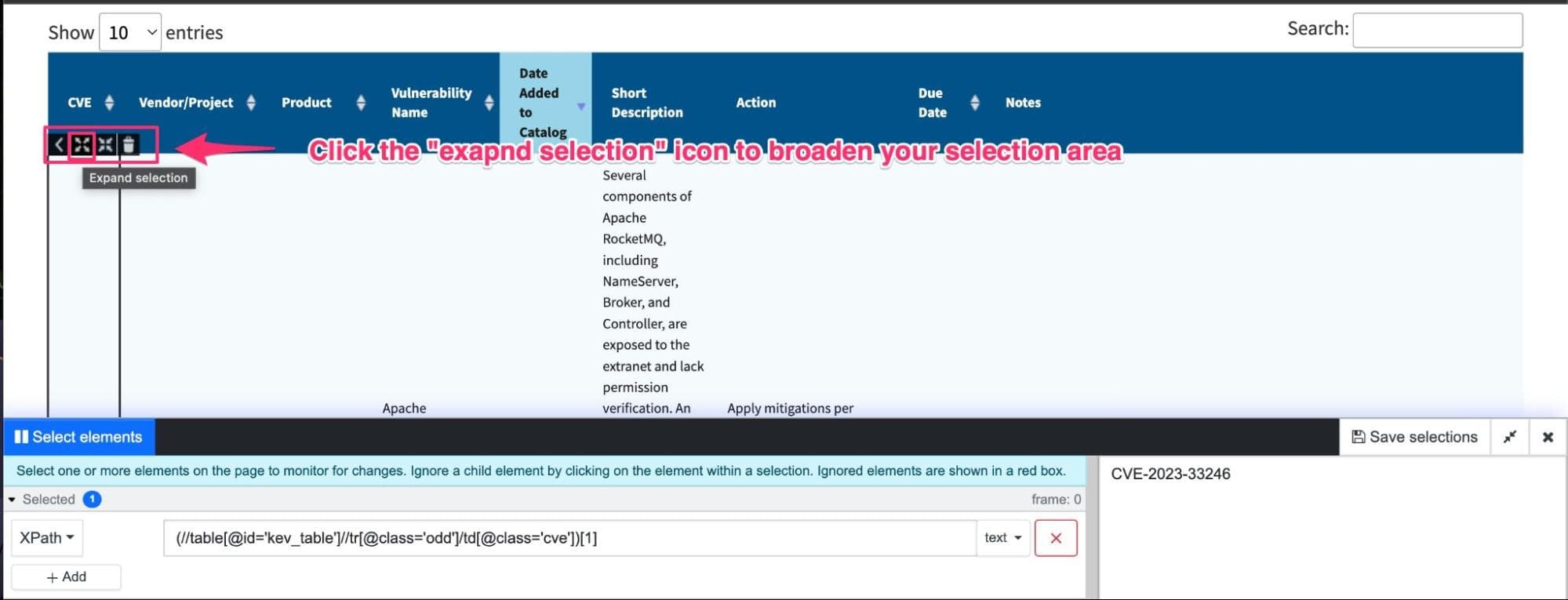
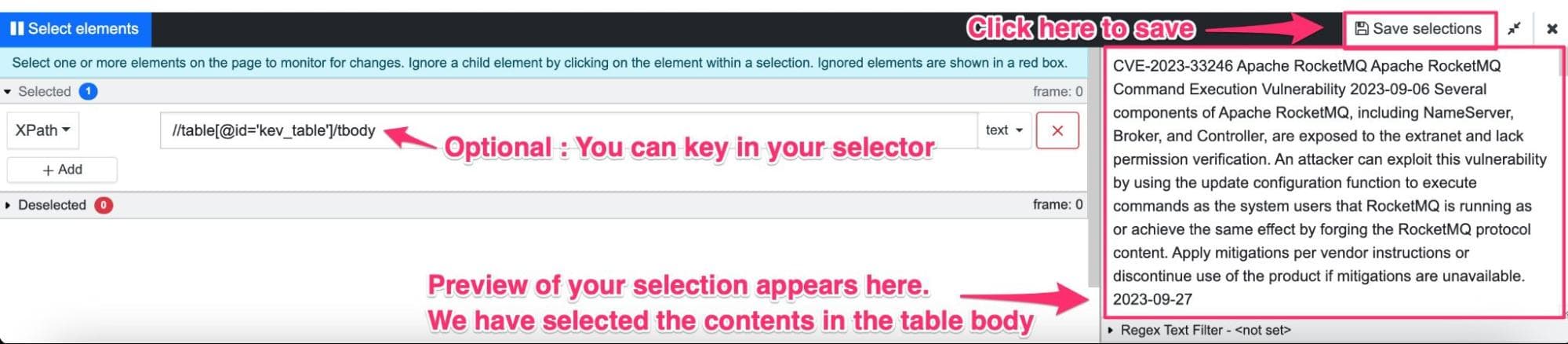
Step 3: Notice the selection will appear in the preview. Once you are satisfied with your selection, click “Save selection.”
Note: Distill allows you to find and add your own selectors. You can either use CSS selectors or XPath selectors. Leverage these to make your selections more refined and accurate.
Step 4: You will be led to the “options page,” where you can set up your CVE monitor. You can choose the device where the checks happen, set a frequency for the checks, and choose an alert mode to receive updates. Once you are all set, click “Save.”
Now, your monitor has been added to your watchlist. Distill will notify you whenever a new entry is made in the Known Exploited Vulnerabilities Catalog. This is a set-up to automatically track the CVE list for threat updates at your chosen frequency, keeping you informed about cybersecurity threats in real-time and ensuring your systems are compliant with standards
In the free plan, you only get access to 30 email alerts a month, be careful not to exhaust them. Check out the subscription plans to compare features that suit your tracking requirement.
You can download this JSON file of a pre-configured monitor that tracks the CVE report for updates.
Download monitor JSON for CISA CVE updates.How to track a CVE RSS feed?
Most CVE lists are also maintained in an RSS feed for you to get all the aggregated information needed for threat intelligence. You can track the one available at https://cve.report/cve.rss or https://nvd.nist.gov/nvd-rss.xml. Tracking this allows you to receive real-time updates as new CVE reports are published. You can use Distill to monitor the RSS feed for updates and set up notifications based on your preference. Be it based on the threat type, name, ID, or other keywords, you choose the conditions that should be met to get an alert.
Follow these steps to set up CVE RSS feed alerts:
Step 1: In your Watchlist, click on “Add monitor.” This will open a drop-down list of options. Select “Feed.”
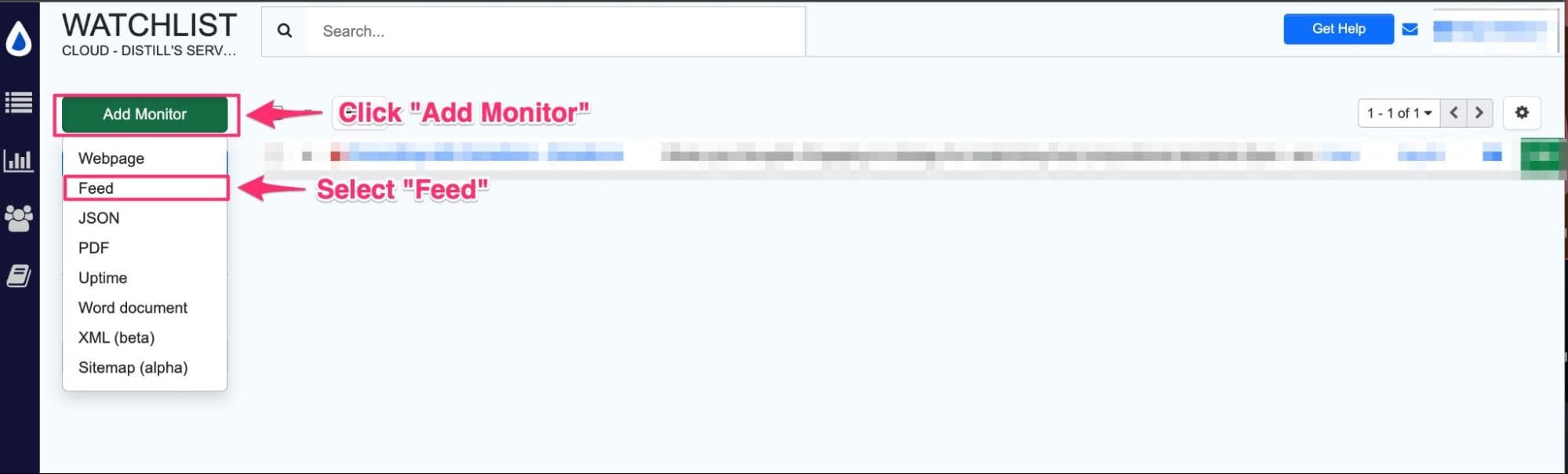
Step 2: Paste the URL of the CVE feed you wish to monitor and then click “Go.” In our case, we will use this feed: https://nvd.nist.gov/nvd-rss.xml
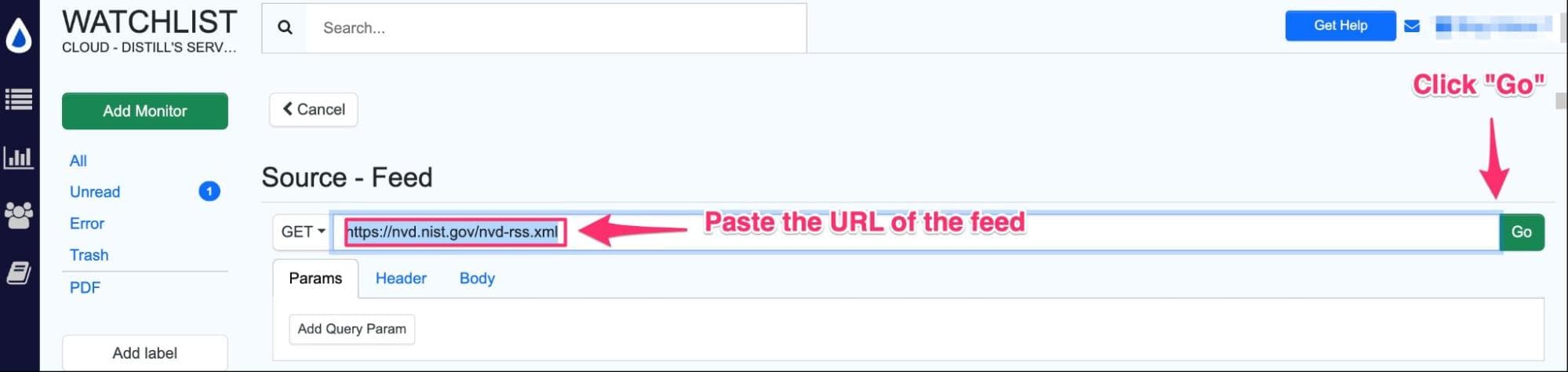
Step 3: Distill parses the CVE feed content, and you should see it appear as below. Now click the “Select” button to set up monitoring the feed.
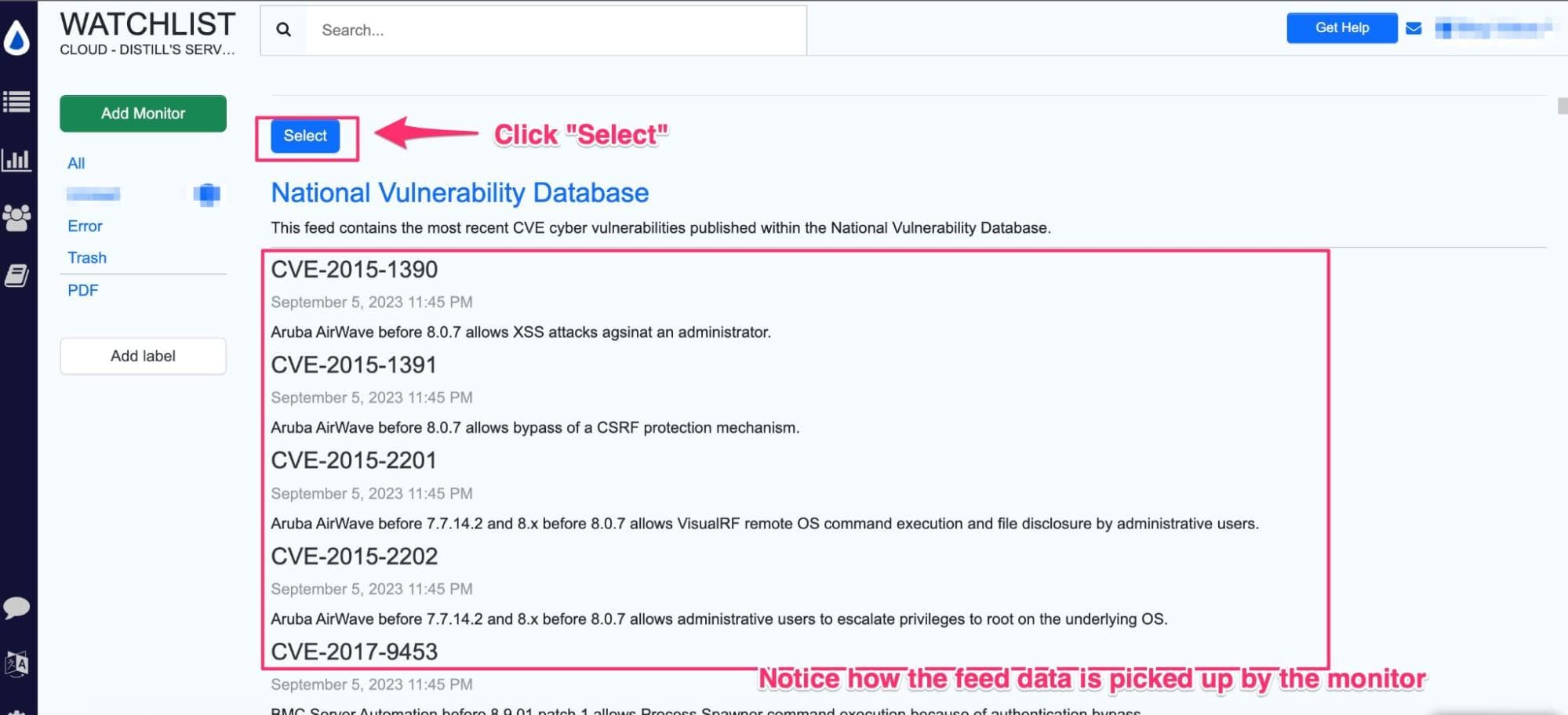
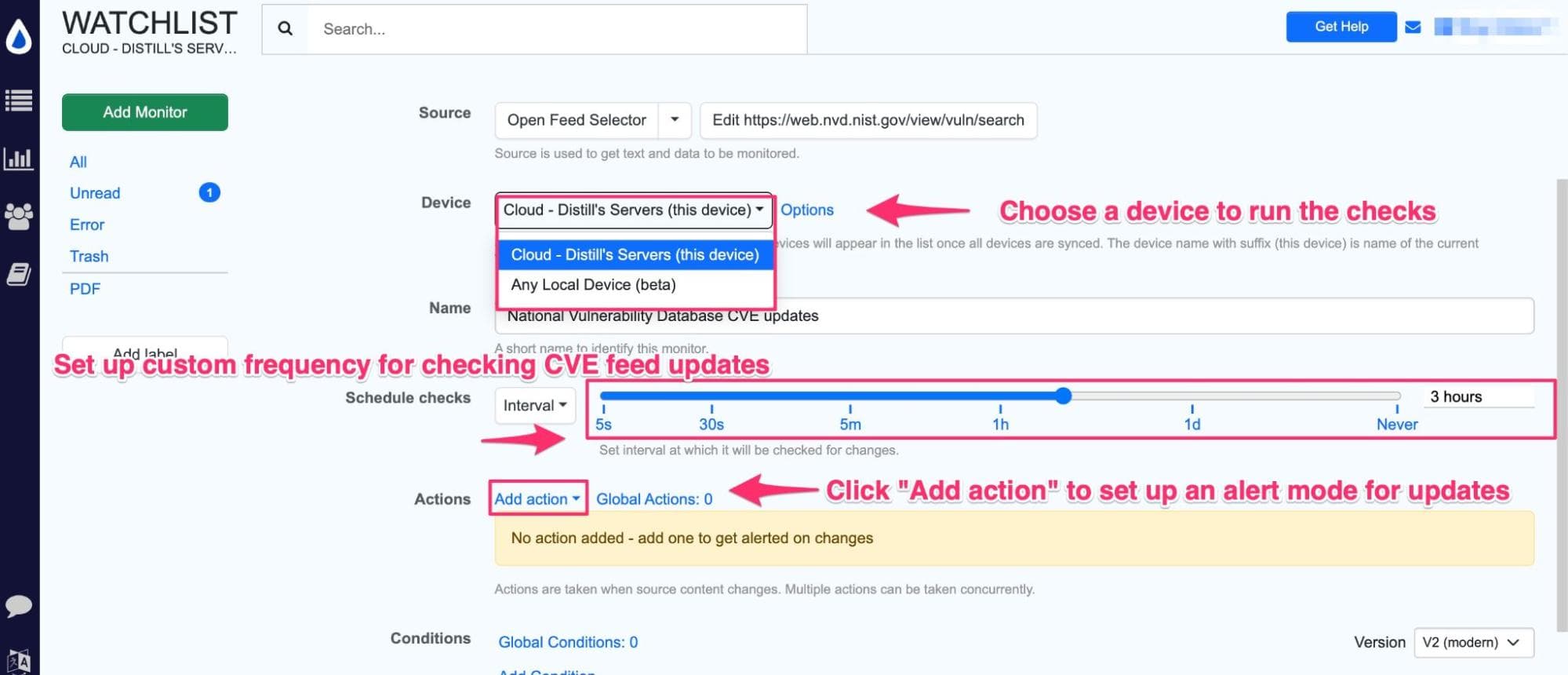
Step 4: You will now be led to the Options page to configure your feed monitor. Here you can choose a device to run your checks on. Here’s more information on the differences between a local and a cloud monitor.
You can set the frequency you want to check the feed for updates and even choose alert modes by clicking “Add Action.”
Alternatively, you can follow this video tutorial on monitoring RSS feeds.
Distill will monitor the feed at the set frequency and notify you whenever there is an update. It even allows you to add conditions to track updates. The conditions could include keywords regarding the vulnerabilities, software under threat, or patch-related to your specific systems.
You can read more about conditions here. Whenever the update to the feed fulfills the condition, Distill will send you a notification. This way, you can filter your alerts and reduce false positives.
To make things easier for you here is a downloadable JSON file of a pre-configured monitor that tracks the CVE RSS feeds for updates. You can simply import this monitor and configure your preferred notification mode by editing the monitor. Read more about importing JSON here.
Download monitor JSON for CVE RSS feed updates.Conclusion
You now have a fair idea about tracking CVE reports and staying vigilant against potential vulnerabilities and threats. By leveraging Distill’s automated monitoring capabilities, security teams can receive timely alerts and updates, allowing for proactive risk mitigation
Checkout our Cybersecurity solutions to learn about using Distill for website defacement monitoring and cybersecurity alerts.
You can download Distill for free today. It is available as a web app, browser extension and as iOS app and Android app.
Please feel free to reach out to us on Distill Forums in case you have any queries or need assistance while setting CVE updates tracker.
 Distill
Distill