Cryptocurrency Security Guide
Without a central authority overseeing security, cryptocurrencies are vulnerable to various threats. :
- Your wallet may be hacked.
- Your PC may be captured by a virus designed to steal bitcoins.
- You may make a mistake in a recipient’s wallet address and send money in an unknown direction with no chance of reversing a transaction.
- You may forget to back up your hardware wallet, accidentally break it and lose your crypto savings.
Scared already? But don’t freak out just yet - we’ve got your back. Forewarned is forearmed: Protecting your cryptocurrencies doesn’t have to be super difficult, especially if you know where to start.. In this article, we will share some detailed tips that you can use right now to ensure the full security of your precious bitcoins.
Tip #1. Add 2nd layer of security using 2FA/MFA
Two-factor authentication adds a second layer of security to your account. When enabled, you have to type a one-time 6-digit password that only you can access. These passwords change every 30 seconds, which leaves hackers with slim chances to break into your account by trying random numbers.
Keep in mind adding MFA doesn’t make your crypto assets hack-proof. The security added by any MFA strategy is as strong as the authentication methods chosen, so use a combination of credentials that are harder to hack.
MFA providers offer various security options. Some options like SMS/phone/email OTPs and TOTPs, and mobile push-based authentication are reliable if managed well. As far as reputation goes, more reliable options include authenticator apps, biometric verification, hardware keys, and smart cards.
If you have not already done this, it’s time you get started
Step 1. Install the Google Authenticator App on your mobile from your app store. Another reliable service that you can use is Authy.

Note that such services are more secure than SMS as telecommunication lines can be tracked by third-parties.
Step 2. Log in to your exchange and find the “Two Factor Authentication” section. Typically, it is located in the security settings.
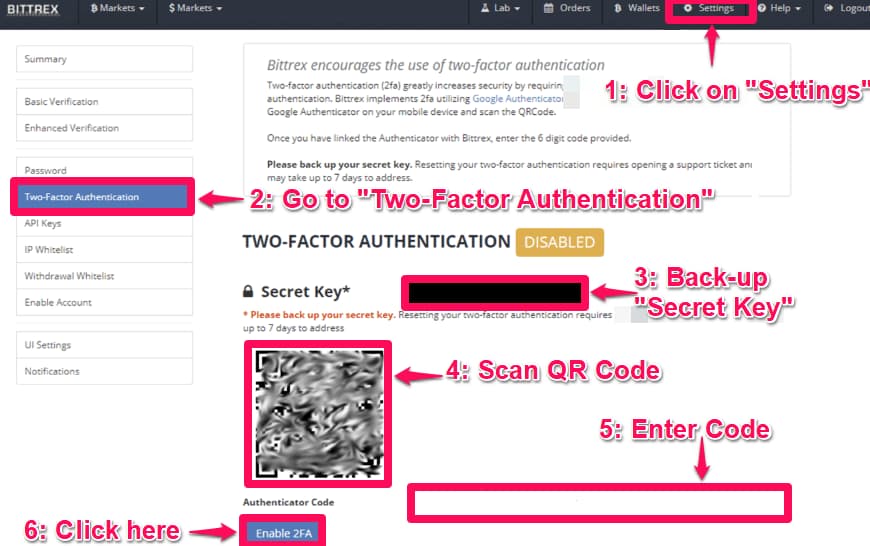
Step 3. Scan the provided QR code in the authentication app on your phone to link it with your account.
That’s it. Every time you log in, check the authentication app for a one-time code.
However, don’t think that 2FA is a magic pill that will guarantee your funds’ security, bypass workarounds exist. In addition to your account on a crypto exchange, set up 2FA on all your online accounts that can be associated with your crypto savings in any way: your mailbox, your accounts on social media, Whatsapp, Telegram, etc.
Also, once the 2FA is enabled, ensure it works properly before you upload any funds. The author of the article had a tough evening trying to access his account on Huobi until he found out what the bug was about. Google Authenticate works a bit asynchronously when linked to Huobi, and the only way to break through the 2FA is to type the sacramental code in a couple of seconds before it expires
Tip #2. Keep track of your wallet transactions to spot any suspicious activity.
Set up a monitoring tool such as Distill on your wallet’s public address. This would notify you if any suspicious transaction occurs.
Such a tool is a perfect addition to any long-term investor with a diversified portfolio.
If you have many different coins and tokens that you hold and don’t use for daily transactions, it will be very useful to receive notifications via email, SMS, or Slack about any changes in your wallet. Such a tool will make regular checks on whether your funds are still in place and give you peace of mind without having to log in to your wallet.
Step 1. Install Distill’s Web Monitor for your Browser (Available for Chrome, Firefox & Opera)
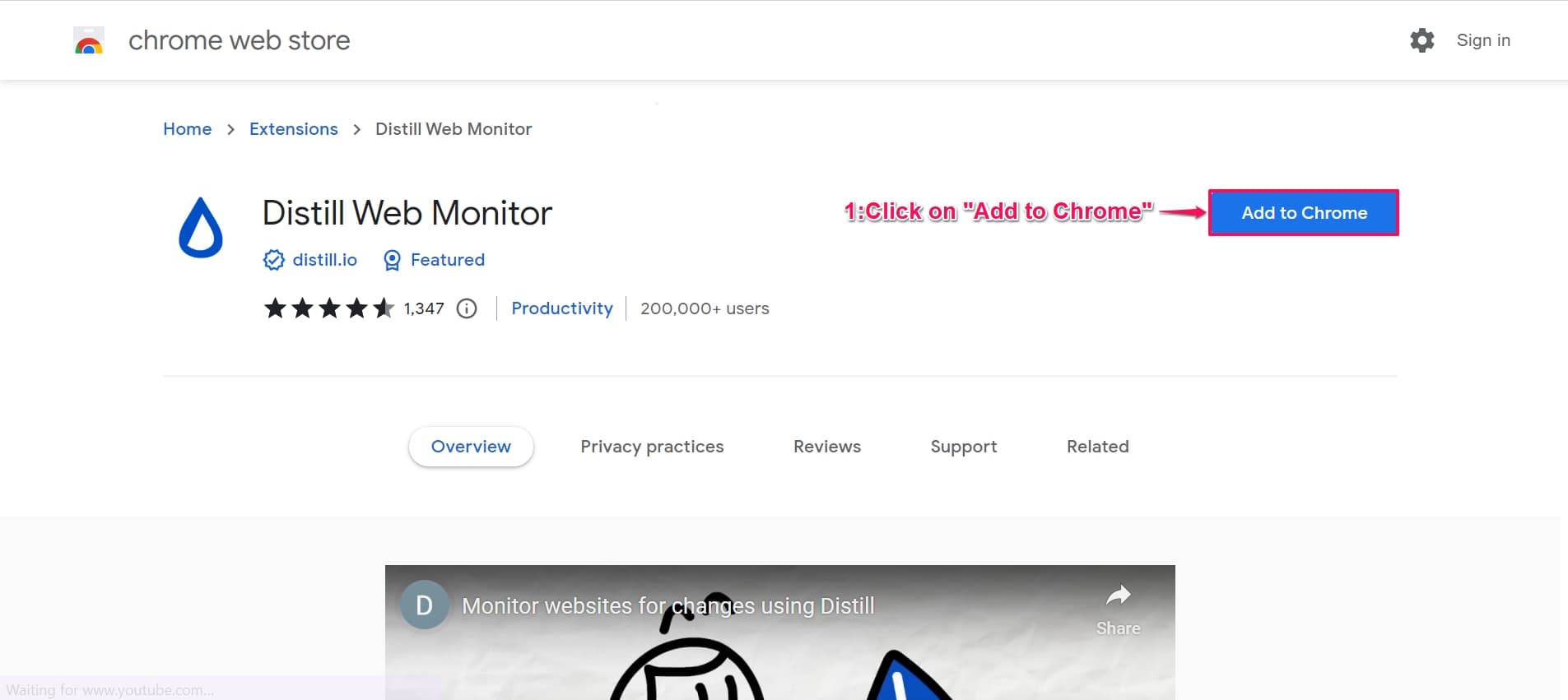
Step 2. Find your Public Address/Key from the wallet (This is the address/key that you use to receive cryptocurrency from someone). It generally looks like this “35hK24tcLEWcgNA4JxpvbkNkoAcDGqQPsP” 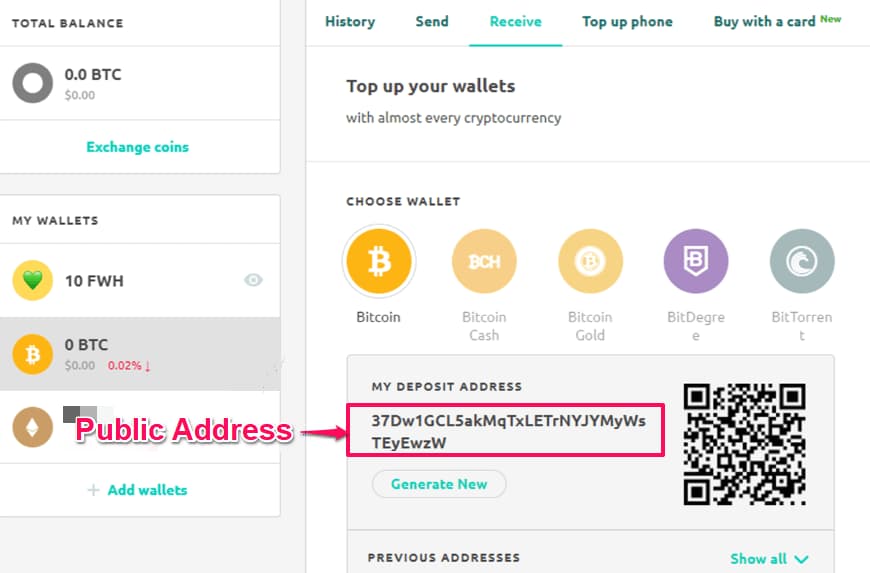
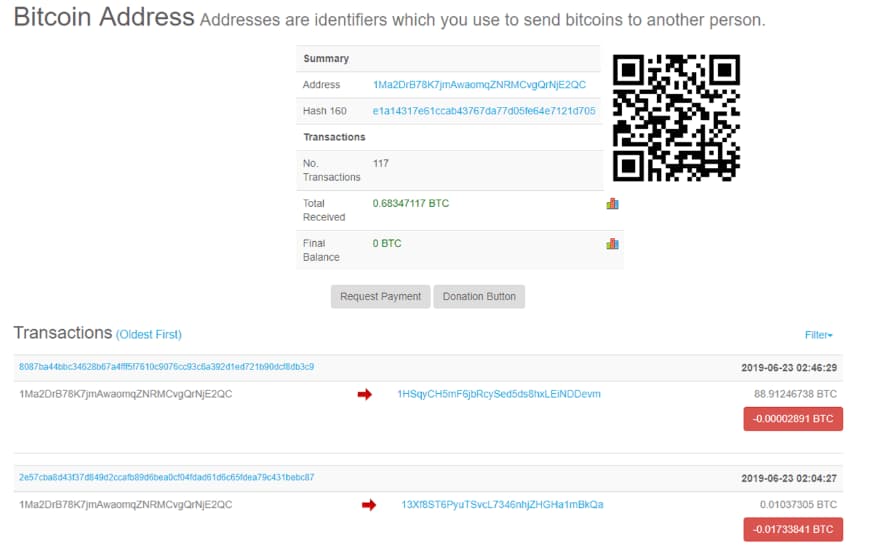
Step 3. Go to Blockchain.info and Enter your ‘Public Address/Key’ and press search or alternatively if it’s BTC wallet: https://www.blockchain.com/btc/address/{YOUR_PUBLIC_ADDRESS}
Step 4. Click on Distill’s Plugin icon (upper left of your browser) and ‘Select parts of page’
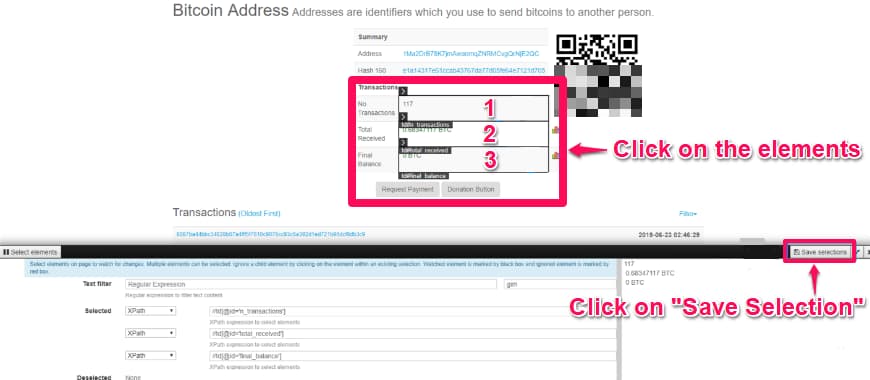
Step 5. Click on the values of ‘No. of transactions’, ‘Total Received’ and ‘Final Balance’. Save your selections.
Step 6. Give your monitor a ‘Name’, select interval for monitoring and assign an action.
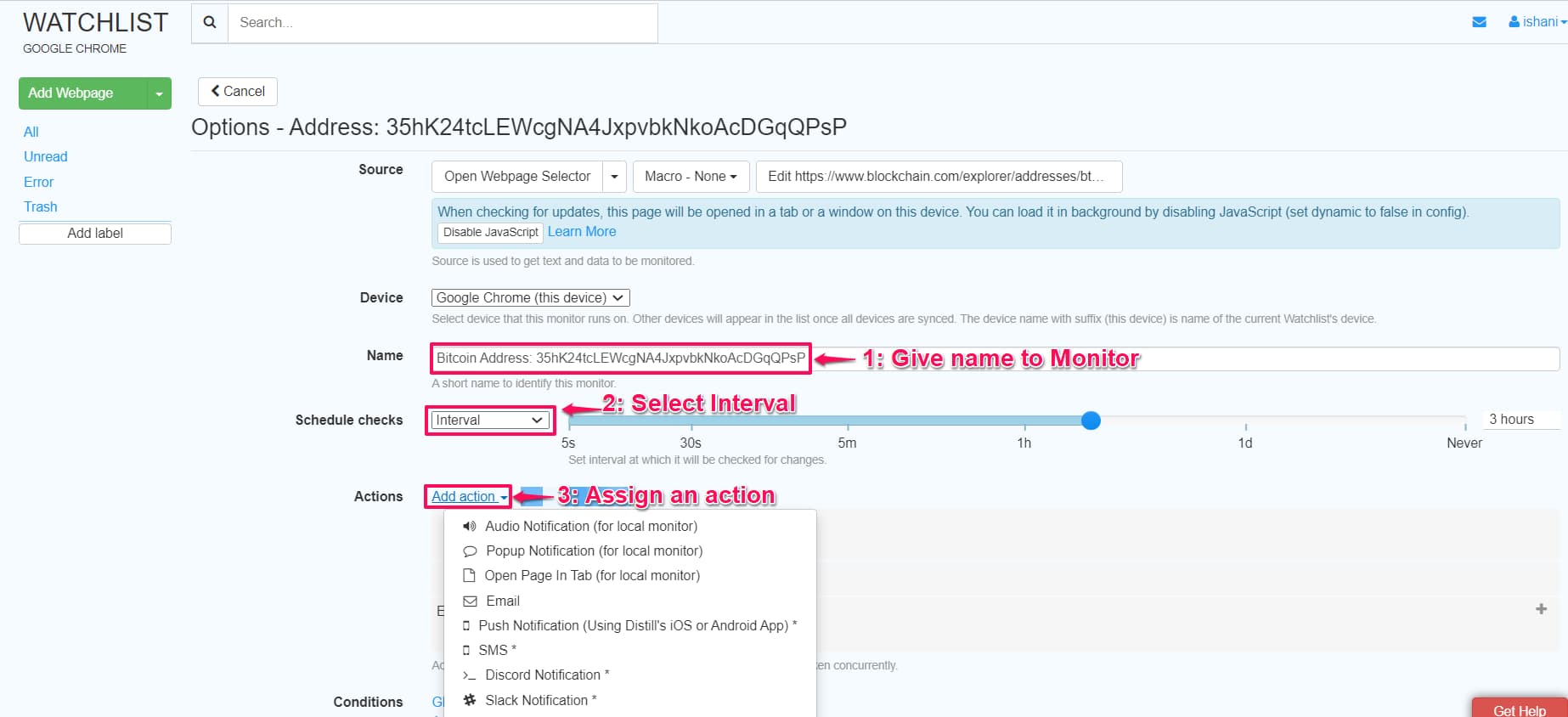
Note: You can track 25 webpages for FREE and receive email notifications on change. If you want more webpages or sms/app notifications, check the plans here.
That’s it. You will now get a notification if any transaction occurs on your wallet.
You can and probably should also set up a tracker on your exchange’s public wallet address (like this) to get notified about any major transactions.
Tip #3. Distribute your currencies among multiple wallets
We all know old wisdom about not putting all your eggs into one basket. Get yourself as many wallets as possible and split your funds amongst them. Thus, if your money is stolen from one of them, that will not end the world.
It may be challenging to purchase several cold wallets as they are far from cheap. But you don’t have to focus solely on them as other choices are aplenty.
Exchange Wallets (Only for what you plan to Trade)
An online exchange is the last place you should want to store a large amount of crypto. An exchange is not a bank to sign an agreement in blood to protect your funds by all means.
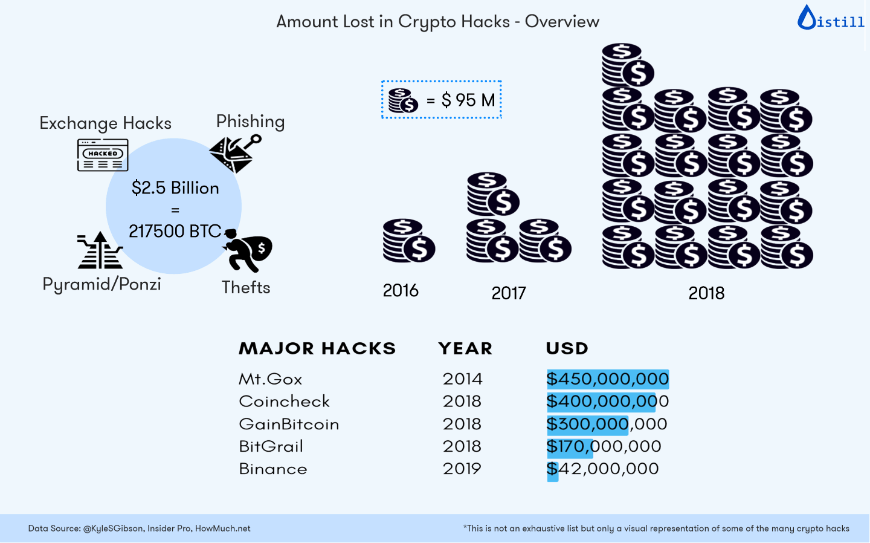
With exchanges, you lose control over your money as you simply entrust it to the third party. If a platform gets hacked, the chances that you will never see your funds again are pretty high. Mt.Gox in 2012; Bitfinex and Bitstamp in 2015; Binance in 2018 - the list of scandalous thefts may go on forever.
![Crypto Exchange Hacks [ 2015 - 2019 ] crypto exchange hacks](images/image-10.jpg)
Yes, many of them claim to store a significant portion of reserve funds on cold wallets that are (almost) as secure as an account in a Swiss bank. But who can check if what they say is true?
Bottom Line: Don’t store a significant sum in your exchange wallet. Only what you plan to sell in the short term.
If you have a significant amount of crypto lying in your exchange wallet, follow the below steps to distribute them right now:
Mobile Wallets (Only for what you plan to Spend)
Here are some of the many good mobile wallets: Mycelium, Breadwallet, Edge, BitPay.
Step 1. Install the Wallet App (say BitPay) on your mobile from your app store.
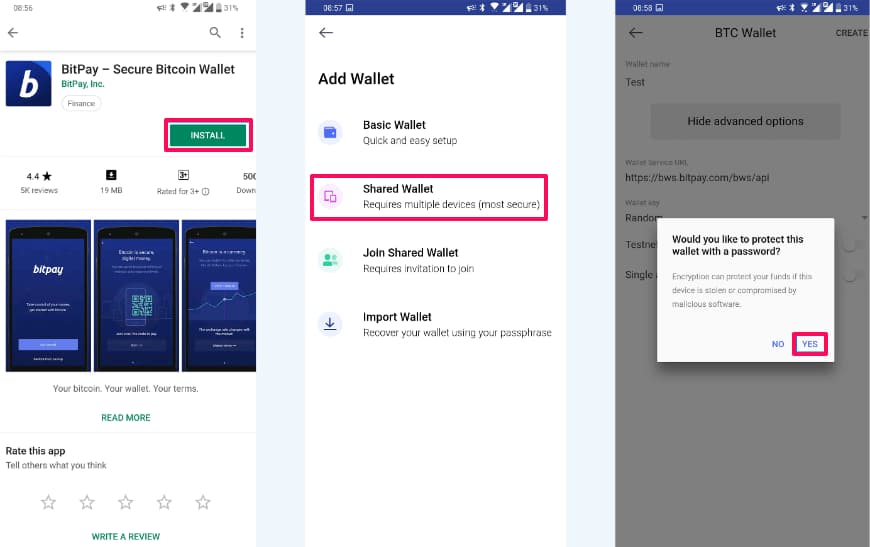
Step 2. Create a new wallet for the currency you wish to spend/receive
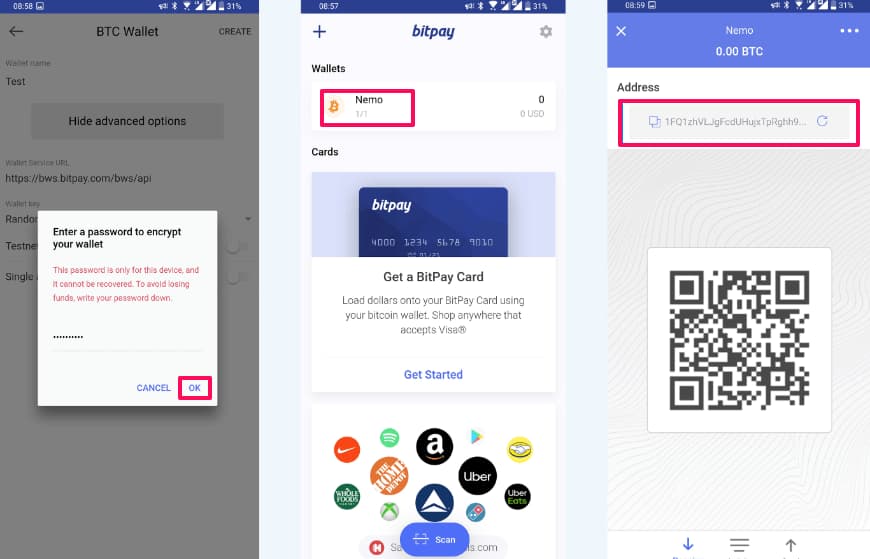
Step 3. Transfer the amount of crypto you plan to spend from main source (your exchange)
Done! You can repeat these steps for as many wallets as you want.
While most mobile apps designed for storing crypto represent hot wallets with a low level of security, recently, there was a new release from Samsung with a built-in cold wallet. Yes, such a wallet would be good protection from online hackers, but all the same, it will not save you from a pocket thief
Cold Wallets (For Everything Else)
A cold wallet/ hardware wallet is a physical, electronic device built for the sole purpose of securing crypto coins. It must be connected to your computer or phone before crypto transfer occurs, keeping your private keys separate from vulnerable, internet-connected devices. A Tech journalist lost $30,000 worth of Ethereum because he stored his private keys on the cloud and not in a hardware wallet. Don’t make this mistake. While cold wallets can help to secure your cryptocurrencies, it’s important to note that they are not foolproof, and there are still risks involved. For example, the wallet could be lost or stolen. It’s important to take additional precautions, such as keeping the wallet in a secure location and creating backups, to ensure the safety of your cryptocurrencies
The two most popular Bitcoin and cryptocurrency hardware wallet brands are:
P.S: If you did follow this tip and distributed your crypto, go back to Tip#1 and Tip#2 and re-do it. Do it right now!
Tip #4. Delete all remote-access software
Programs such as Zoom (Yes! Zoom), TeamViewer or Ammyy Admin have numerous security holes. Don’t Believe me, see some examples yourself.
Having such remote-access software can overwrite all safety precautions taken such as 2FA, since it gives attackers access to your entire computer with just a string of characters.
Bottom-line: Never install such software on your computer, especially not on one containing your private keys. And if you have one of them installed, DELETE/UNINSTALL them right now!
Tip #5 Use the "advanced recovery phrase" to Store Multiple Backups of Seed Phrase
When it comes to the security of your data, be it your passport scan or your lovely bitcoins, backup is something that may once save your day. Here’s how you can do it.
Step 1. Get your seed phrase.
Secure wallets provide you with a seed or mnemonic phrase during installation, which can help you restore your funds in case your hard drive crashes, or you need to recover your funds on another device for any other reason. You can find it in the security settings.

Step 2. Make several physical copies of your seed phrase.
Typically, seed phrases represent a mix of 12 or 24 words that are not related to each other. It’s challenging to learn them all by heart unless you have a phenomenal memory, so you’d better write it down and make several copies to keep in different places.
Step 3. Distribute the copies across multiple locations.
Give one to your Mom for safekeeping, copy-paste it into your encrypted cell on AWS storage, put one more under your mattress. The more reserve copies you create and the more locations you find where to hide them, the safer your funds will be.
Step 4. Setup an ‘advance recovery phrase’ - This passphrase is essentially a password added to your 24-word recovery phrase.
-
To access passphrase-protected accounts, an attacker will need your recovery phrase as well as your secret passphrase.
-
Each different passphrase unlocks a unique set of accounts. You can use as many passphrases as you like.
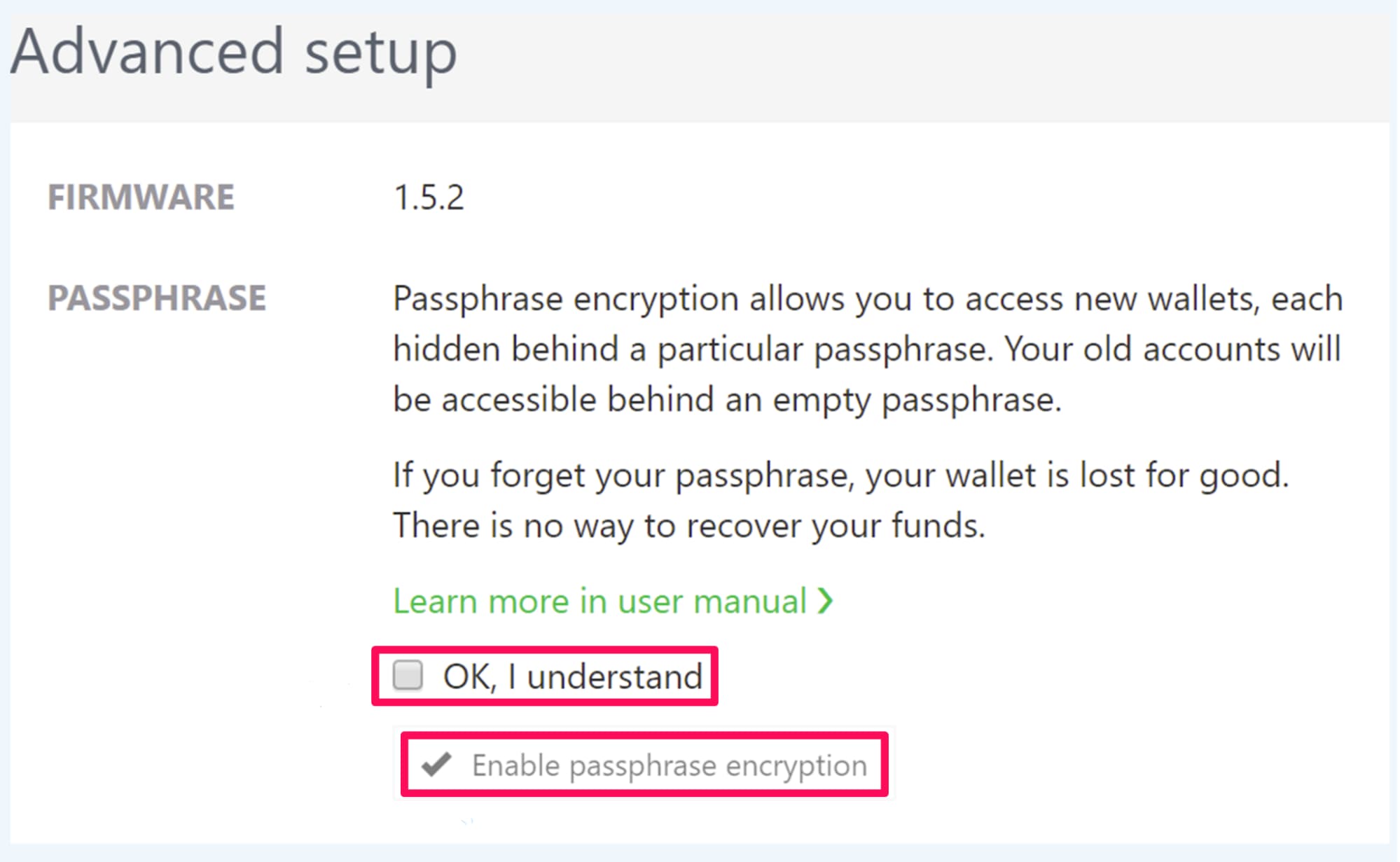
Now if your device with bitcoins is crashed, all you need to do is to re-install your wallet somewhere else and type your mnemonic recovery phrase and passphrase at the first launch. All your precious coins will be there.
Tip #6. Decrease your OS vulnerability using Linux.
Linux-based systems are more secure than Windows by design. Initially created by geeks and for geeks, they are far from user-friendly, which cuts down the significant portion of the audience and makes them less desirable for hackers.
To install a piece of software on Windows, users typically download executable files. Unless you download such a file from the official provider, you may never be sure it is not infected.
When using Linux, the software is installed via a command-line interface from a public repository where all the viruses are immediately spotted by the restless community. This makes the chances of catching a virus negligible.
If you have never used Linux before, try a lightweight and user friendly Linux distribution (called “distros”), such as Ubuntu. If you are looking for the most secure OS on the planet right now, check out - Qube OS.
How to Install Linux? See the step-by-step guide here.
Note: Never download the ISO from unrecognized source (like torrents) as they will certainly be compromised.
Tip #7. Disable Auto-Updates for your wallet
Crypto wallets are periodically updated to stand against the latest security threats. Failing to update your wallet may expose your funds, so you should closely monitor desktop and mobile wallets for new releases.
However, don’t rush to download the new version as soon as it is available, and disable auto-updates. Sometimes new versions are released with bugs that are cleared off only after a heap of angry comments appears. Wait for 2-3 days and update the wallet only if all is quiet.
If you followed Tip #2, Setup a distill monitor on your wallet’s update page and you are sorted.
Tip #8. Tokenize your personal data
Tokenization replaces sensitive data with a unique, randomly generated token that can be used to store, manage, and handle crypto transactions. Tokens generated are irreversible and indecipherable, unlike encrypted data, which can be decrypted.
It helps turn personal financial data, such as an account number, into a random string of characters called a token that has no meaningful value if breached. It can serve as a reference to the original data, but hackers cannot use it to decipher your personal information tied to your digital assets.
Tip #9. No Ads, No Phishing, No Malware
Most hackers use highly tempting phishing ads to get users to click on it and once the user clicks on it, the ad would install malware on your system. Since, it’s difficult to distinguish between a safe and malware infected ads, we recommend installing an ad blocker in your browser.
Here’s a list of ad blocker extensions we have personally used and would recommend too :
As a general rule, with or without an adblocker, it is advisable not to click on any advertisement. Ever!
Consider using Anti-Virus software.
They can help add an additional layer of security. It can help identify and block phishing attacks, protecting you from falling victim to these scams. They improve the overall security of your computer and protect against a wide range of threats, including malware, viruses, and phishing attacks.
Additionally, using a firewall can help protect your cryptocurrency assets by blocking malware and unauthorized access, detecting suspicious activity, and increasing overall network security. It’s important to use a firewall, along with other security measures like strong passwords and two-factor authentication.
Tip #10. Block invisible Trackers.
Crypto hackers use spy ads or set ‘invisible’ trackers to monitor your online activity without your permission.
To stay safe from such sneaky hackers, download Privacy Badger extension in your browser - Chrome / Firefox / Opera.
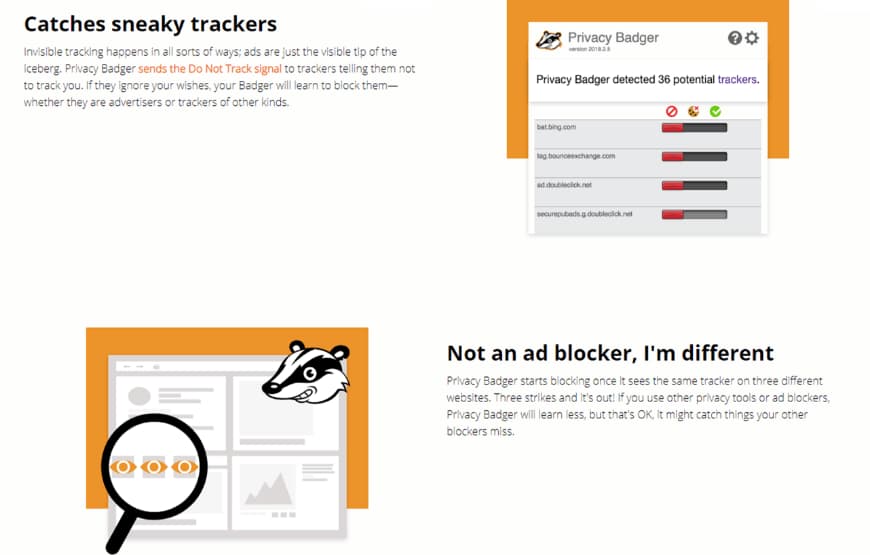
It blocks ads and tracking cookies that do not respect the ‘Do Not Track’ setting in a user’s web browser. Now, when you visit any site, in case it finds a tracker on the website, it will give a warning and block the tracker.
Tip #11. Secure mail service for crypto - ProtonMail
While most crypto-currency traders use Google or Yahoo email accounts to trade cryptocurrency, it might not be the best way.
According to the terms and conditions of Gmail, you grant permission to Google to read your email and track your activity even if you exit Gmail. Such tracking puts you and your login credentials and transactional history at a high risk of getting hacked.
Rather, a far safer option is to use ProtonMail for emails. ProtonMail does not read your email or track your activity in any form.
Tip #12. Secure browsing with these extensions
Phishing is one of the most common ways hackers can steal your cryptocurrency. Hackers create a phishing page that looks so tempting that you just find yourself clicking on it. They generally do this by creating a replica of cryptocurrency exchanges and once you click on it, you expose your private information, which hackers can use to gain access to your sensitive online accounts.
To protect yourself from phishing attacks, do not click on websites that have HTTP instead of HTTPS in the address bar, and if the website looks weird, just don’t click on it.
Also, download these extensions in your browser to know if the website is safe :
-
HTTPS Everywhere (Chrome / Firefox / Opera)
HTTPS Everywhere automatically switches sites from insecure “http” to secure “https”. It will protect you against many forms of surveillance and account hijacking, and some forms of censorship. This helps encrypt communications with many major websites, making your browsing more secure.
-
Netcraft Extension (Chrome / Firefox / Opera)
This extension allows you to see the risk rating of every site and protect against phishing attacks by showing you a rating given by existing users of the extensions i.e When members report a suspicious link, the extension prevents all users from accessing the site. Netcraft processes reports of fraudulent URLs from various sources and proactively searches for new fraudulent sites. A great feature of this extension is its ability to trap XSS and other suspicious URLs which contain characters highly likely to deceive.
-
Cookie AutoDelete (Chrome / Firefox)
HTTP Cookie is data sent from a website and stored on the user’s computer by the user’s web browser while the user is browsing. Hackers use cookies to hijack and retrieve information such as passwords which could be stored by crypto-exchanges in forms of cookies.
To protect your data, you need to delete all cookies especially from crypto-related sites. You can do it automatically by installing an extension like Cookie AutoDelete. It will automatically delete the cookies stored by the website when you exit it.
Tip #13. Secure and Encrypt your data using your own VPN
VPNs will protect your data using military-grade encryption and make it harder to track while trading. You may want to configure the VPN to only protect your crypto activities - if it slows down your internet).
VPNs encrypt your internet connection, which can help to protect your personal information and data from being intercepted by hackers or other third parties. This can be especially important when you are accessing sensitive information, such as your cryptocurrency exchange account or wallet.
VPNs allow you to browse the internet anonymously by hiding your IP address. This can help to protect your identity and make it harder for others to track your online activities. When choosing a VPN, keep in mind:
- That it does not store user logs (as they can potentially be matched to your traffic)
- Free VPNs may fund themselves by selling your data, leak your identity or run ads that may be dangerous while trading )
We recommend using NordVPN or ExpressVPN. Check out their detailed tutorials on how to set it up for your OS. If you want to create your own VPN, you can do it in 5 minutes by following the details here
Tip #14. Use Password Generators.
One of the most popular passwords specified by users of all devices globally is “123456”. The password “password” is the second in line, but it doesn’t make hackers’ lives any harder.
AAvoid using passwords that consist of pure numbers, as their combinations are limited and easily guessed. Avoid using passwords that contain a single word, too, as it can be easily guessed with the help of a dictionary.
“Passwords are like underwear: you don’t let people see it, you should change it very often, and you shouldn’t share it with strangers.” - Chris Pirillo
The best and the most secure password will consist of a random mix of digits, numbers and special symbols.
Use password generators such as LastPass and KeePass to generate a strong password for your exchange wallets and email account.
Alternatively, to make it easier to memorize, take a line from your favorite song, make every first letter of every word capital and change some letter to special symbols where it’s possible (e.g. S to $, o to 0, etc.).
Tip #15. Have a Kill Switch - Setup Remote Wipe.
Though cryptocurrency cannot be controlled by anybody unless the private keys are compromised, theft of mobiles can occur. The thieves can log into your crypto exchange and gain access to your cryptocurrency.
This could lead to huge losses. Yet, most of us neglect to take measures to protect our cryptocurrency in such situations.
A simple solution, like activating a ‘kill switch’, can save your crypto if your mobile gets stolen. Once activated, the ‘kill switch’ can wipe ALL of your data and lock your phone remotely. As a result, the thief no longer has access to your exchange wallet or any data on your mobile.
It’s possible to setup ‘kill switch’ function on both iOS and Android.
iOS :
Go to Settings » iCloud » Sign in with your Apple ID » Turn on Find My iPhone.
If your phone is lost or stolen, to activate the kill switch:
Step 1. Visit https://www.icloud.com/#find
Step 2. Log in with your Apple ID and set your phone to “lost mode.”
Step 3. You will have the option to remotely wipe all your data and it will be locked.
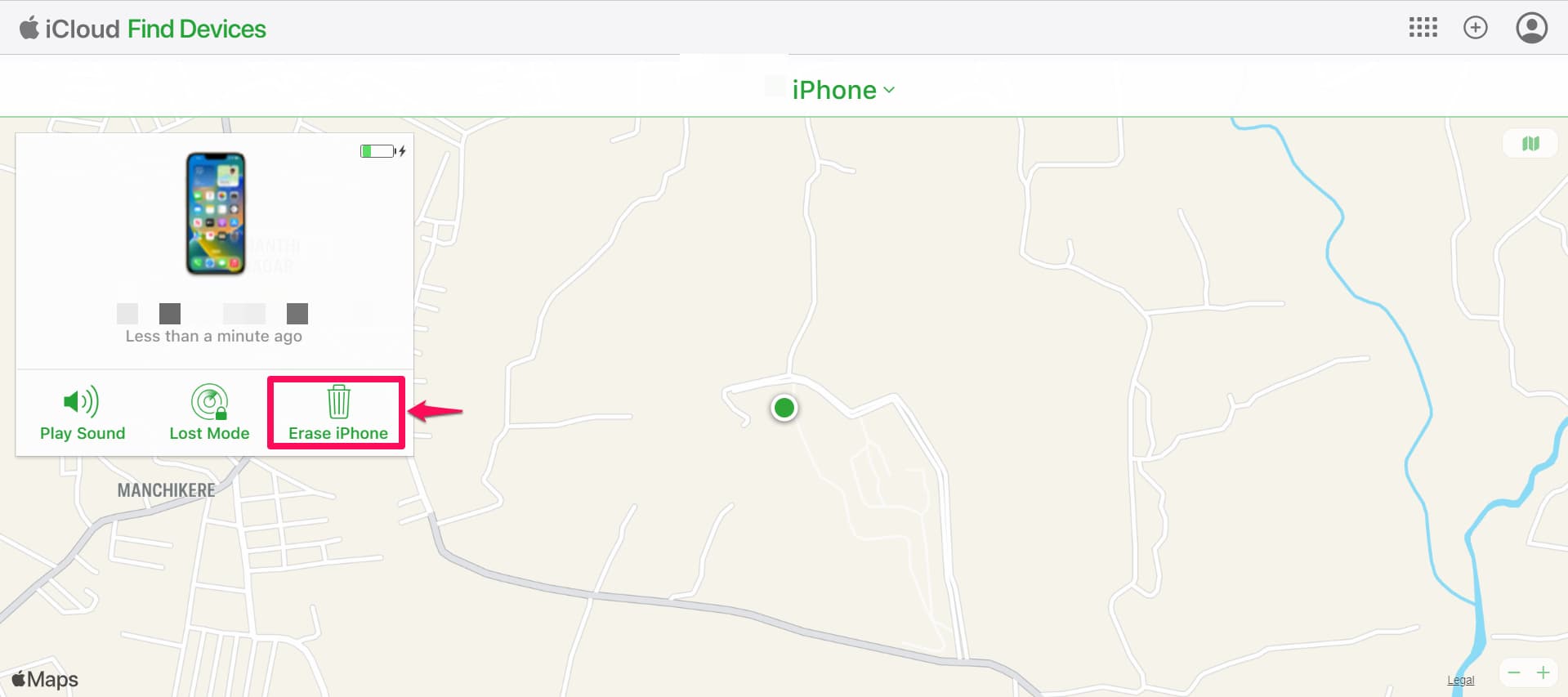
Android :
Step 1. Go to https://www.google.com/android/find and sign in to your Google Account.
Step 2. If you have more than one device, click the lost device at the top of the screen.
Step 3. If your lost device has more than one user profile, sign in with a Google Account that’s on the main profile. On the map, you’ll get info about where the device is.
Step 4. Select Erase. This will permanently delete all data on your device (but might not delete SD cards).
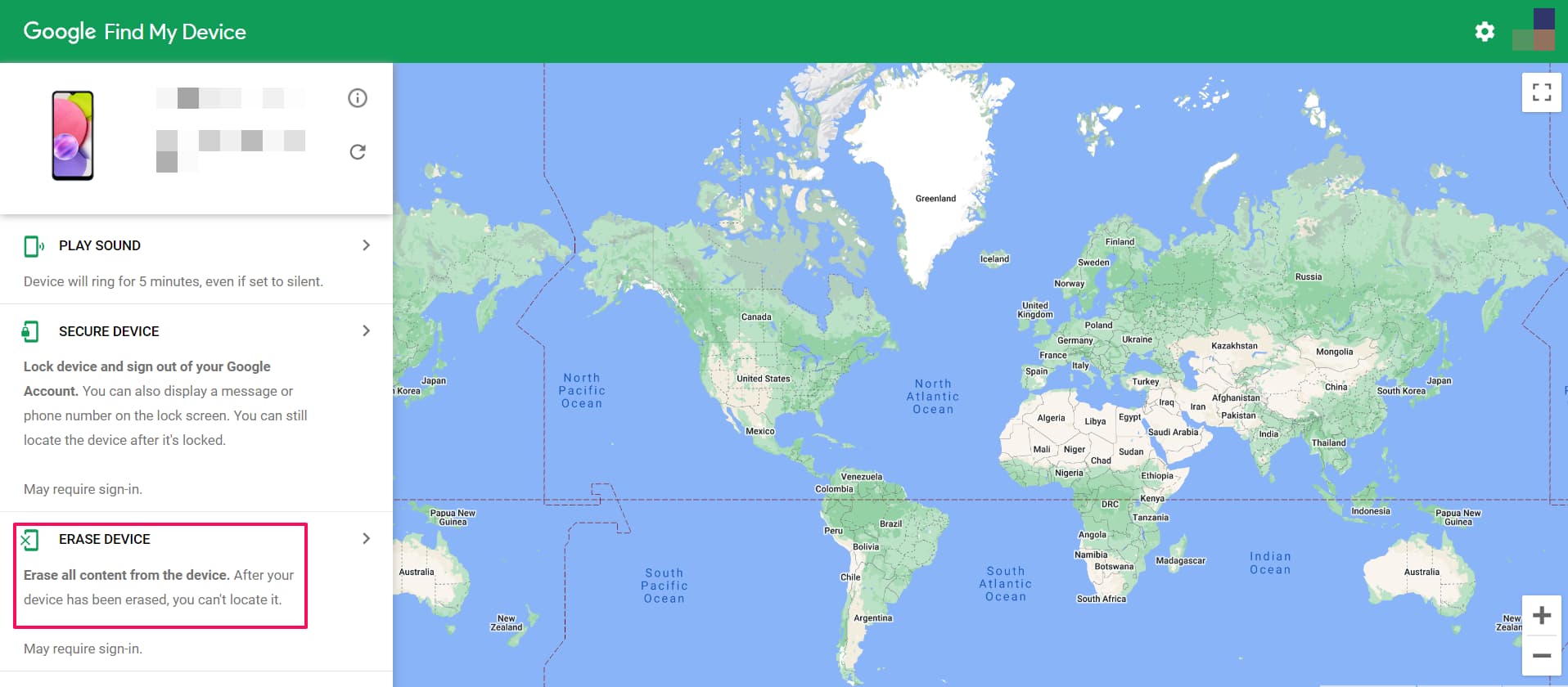
Some cryptocurrency wallets offer a kill switch feature that destroys the private keys associated with the wallet in the event of a security breach or other emergency. This can help to protect the assets in the wallet and prevent unauthorized access to them.
Tip #16. Keep track of latest developments and scams.
Tracking and filtering important cryptocurrency news is a big task but highly important. You need to constantly monitor the latest news that could affect your crypto wallet.
For example - Had people been aware about the attack on Electrum wallet in December 2018, the intensity of the attack could have been controlled. Though Electrum detected and broadcasted the attack, users continued downloading the fake wallet. This resulted in 250 BTC being stolen.
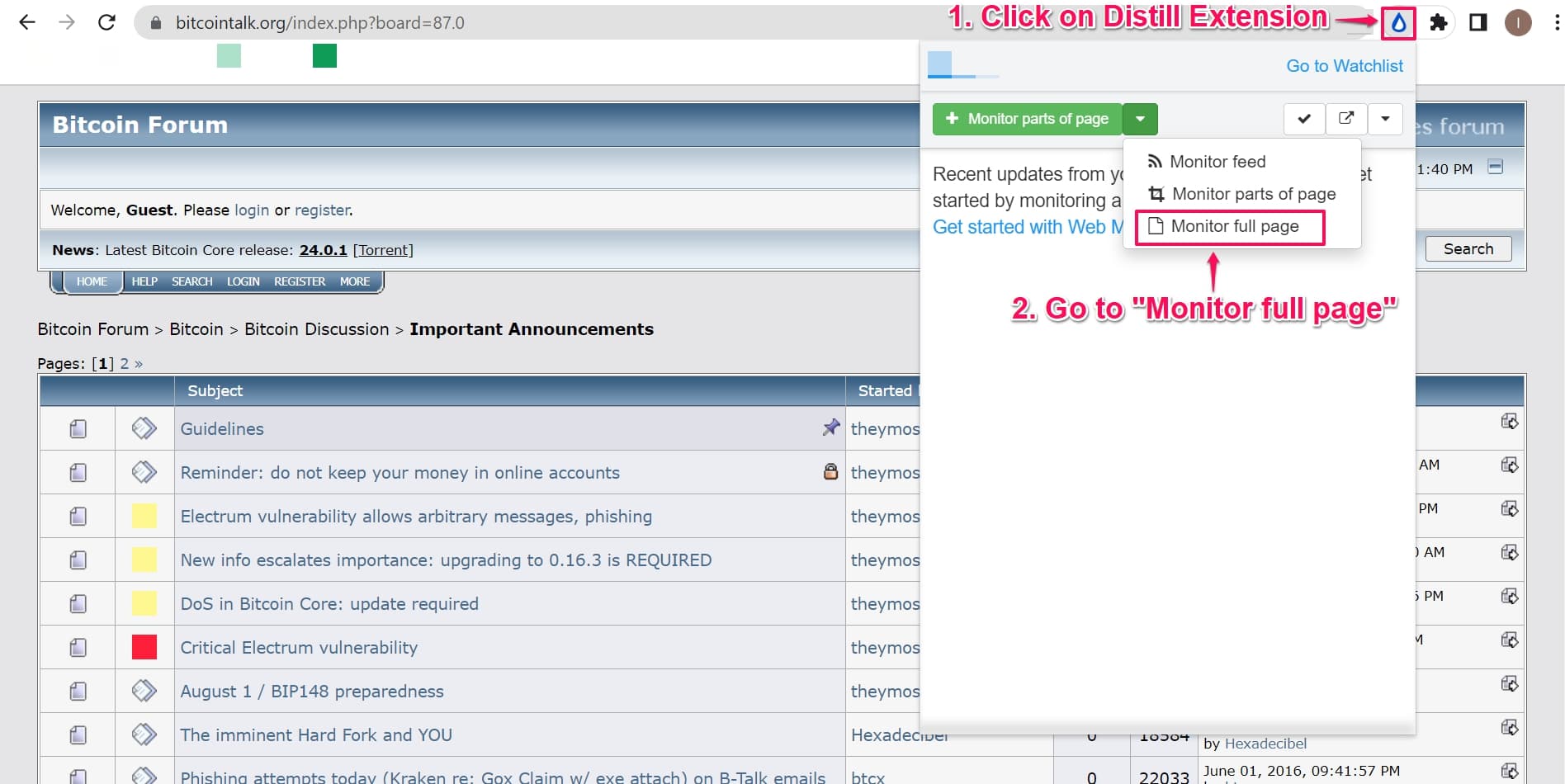
Therefore, monitoring current news and forums using a tool like Distill.io becomes important. Here’s how you can automatically monitor such news:
Step 1. Go to BitcoinTalk Important Announcements
Step 2. Click on Distill.io chrome extension to setup a Distill monitor on Full Page.
Other than the above mentioned steps, you should also:
- Follow relevant Twitter accounts such as - Whale Alerts
- Setup Google alerts to email relevant articles that meet keywords including wallets you use, crypto you invest in and crypto exchanges you trade with.
- Subscribe to newsletters such as Trezor.
You’d also want to remember these Dos and Don’ts.
Share access to your funds with at least one person you can trust.
Not so long ago, the crypto community was struck by the news of QuadrigaCX founder’s death and the loss of all investors’ money (almost $200 million worth of crypto) as he was the only one who had access to the startup’s wallet. Some evil tongues were spreading gossip that it was a nice touch to exit scams and to go away with all the money, but the new proofs have smashed all these rumors.
Don’t be like QuadrigaCX’sQuadrigaCX founder. Let at least one person know how to restore your funds in case something bad happens to you.
Triple-check when making a transaction.
Crypto transactions are irreversible, and any small mistake in a recipient’s address will lead to money loss. Since crypto wallet addresses represent a huge mix of digits and numbers, making a mistake is not that difficult. Never type addresses manually; only copy and paste.
However, even this precaution is not always enough. There are some tricky crypto-stealing viruses that replace the wallet address with the one that belongs to a hacker. Even after you copy-paste the address, attentively check the first and the last few symbols and make sure that they correspond.
Another element you should pay attention to is the size of the transaction fee. Not so long ago, there was a peculiar piece of news on the web about someone paying the fee of 2100 ether only to send 0.1 ETH. Was it an intentional move to reward miners or a mistake that left the sender with nothing but a big regret? No one can say.

Keep your mouth shut. Shhhhh!
Don’t share publicly - how much crypto you own and where you store it. Envious ears are all around us, and such openness may end badly.
It may be tempting for a bitcoin investor who has woken up rich to share his joy with others, but it’s better not to attract anyone’s attention towards your sudden wealth.
Always double-check the address of an exchange before you log in.
There are numerous phishing websites designed to steal your login and password. Typically, they are designed exactly like reputable exchange platforms and have a similar address (e.g., “Bilttrex” or “Binanse” (Notice the small spelling errors?)). Other phishers are designed exactly like browser wallets, such as Metamask, that pop up on top of your current page.
Don’t fall for such tricks. Always type the address of an exchange manually in the browser and ensure that your wallet appears only after you intentionally click on the app’s icon.
Beware of public WiFi
Public WiFi-s are very dangerous since their hosts may set up their own rules you will never be aware of. For example, they may redirect your browser to a phishing version of an exchange or a wallet. They may collect the data you access on your smartphone or tablet, including passwords.
VPN is your friend!
If there is a dire need to access your crypto funds from public WiFi, use a VPN. The browser Opera has a built-in free VPN available in private mode. For smartphones and tablets, there are numerous apps, such as Turbo VPN. ( More about this in Tip #13).
Summing up
Keeping your crypto funds secure may seem tricky at first glance. Why are there so many dangers and no third party to rely on? Right?!
But if you are keen on using a new system that stands aside from the highly centralized financial world, you should learn to protect your savings yourself. And although all these precautions may seem a bit complicated for less tech-savvy users, you will find that it’s not that hard as soon as you turn them into your daily habits.
In case you have queries on using Distill for your crypto needs, you can reach out to our community fourm.

![Freelance Job Alerts: Upwork & Fiverr Tracker [2025]](/blog/get-instant-alerts-for-new-freelance-job-postings/image/1-a-job-track-banner-image.png)


